Discovering Computers
Chapter 5: Digital Safety and Security
Denial of Service Attack, Bots, Botnet, Zombie Army and more
Digital safety risks
- One of the intents of a cybercriminal may be to extort money, as described on page 204. See this recent video news clip (2014) on NBC; a criminal threatens to wipe out all files if the victims don't pay up.
- What is a white hat hacker? A good guy.
Passwords
Do you have a strong password? Shhhhh! Don't tell me!
Internet and network attacks
Page 23 of chapter 1 and page 106 of chapter 3 discusses malware. Chapters 3 and 4 provide further explanation, along with good tips to help avoid infections. In chapter 5, page 205, additional Internet and network attacks are described.
- Watch the word's hackers live with this mesmerizing map from Norse, an online security company. See how often these attacks occur.
- See online privacy tips, best Android antivirus apps, free-antivirus software (along with reviews), and ways to avoid a virus and network attacks.
- See a list of known malware from Symantec, a leading software company that provides security and other services. Products include Norton antivirus protection.
- Botnets: a bot infected computer that does the bidding of its master is often referred to as a zombie. Bots sneak into unprotected computers. Their goal is to stay hidden until instructed to carry out a task by the master. Read the FBI's Botnet 101: what they are and how to avoid them.
- A zombie army may be used to attack computers and networks and slow down the entire computer network or make it completely unavailable. This is referred to as a Distributed DoS (DDos) attack.
- Watch this short video that describes a DDoS attack and why people may execute such an attack.
- As mentioned on page 207, Yahoo! was attacked in 2000. Other leading websites were under attacked as well.
- Read about a more recent attack in which cyber crooks stole more than $900,000 from a financial institution in California.
- In 2013, PCmag reports a record-breaking DDoS attack
- Learn more about Denial of Service Attacks from CERT.
- Can you identify this malware? Trojan horse or a worm?
- Email spoofing: an official looking email may be used for phishing, spam and virus hoaxes.
- IP spoofing: an introduction (history, how it works, and how to defend against it).
- Safeguard your computers and devices:
- Use antivirus software. Here are some tips to protect your system, recommended software and reviews.
- Disable macros. For example, in Microsoft Excel complete the following:
- Open Excel and then click the File tab to enter back-stage view.
- Next, click Options.
- Click Trust Center on the left and click the Trust Center Settings button.
- Choose one of the Macro Settings to disable all macros.
- Block unauthorized entry to your computer with a firewall.
- The Windows operating system includes a firewall that is on by default. Learn how to check your firewall settings in Windows
- Learn how to configure the firewall on a Mac.
- Third-party software that may be used.
- Learn how to keep your operating system software up-to-date
Information theft
- Russian criminals have stolen more than 1.2 billion username and passwords. What can you do to protect your information?
- What do hackers know about you? Depends on where you may have shopped and accounts on certain sites. Click the merchant/site to find out.
- Try the online Caesar cipher converter.
- There are two basic types of encryption used to transfer information and prevent information theft:
- (1) Private key (symmetric). Same key is used to transfer information. The key must be shared with another person for them to access the information. It is faster, but easier to steal information as only one key is used.
- (2) Public key (asymmetric) uses two keys: public and private. Only the public key is shared with another person for them to access the information. Even if the public key is stolen, information is still safe as the private key is also needed to steal information.
- Watch a video from IT Free training that demonstrates how these keys are used to safe guard information.
- Email connections should be encrypted to protect your information and to help protect your account from being hijacked. A few examples of what you should do are listed below. For more in-depth knowledge, including encrypting email messages, stored email, and encryption programs, see an article from PCworld.
- When checking your email with a browser, be sure the website address (URL) begins with "https" instead of just "http". My Google gmail web site address looks like the following: "https://mail.google.com..."
- When checking your email with a program such as Microsoft Outlook, navigate to the settings. Look for an option something like "This server requires an encrypted connection (SSL)" and be sure it is checked so that it is turned on.
- On mobile device email settings, you may need to navigate to advanced security options. Look for an option to "Encrypt all email."
- Digital Signatures are used to verify the identiy of the message sender. Digital Signatures can be purchased from a certificate authority such as adobe, microsoft and other organizations.
- Digital certificates are notices that guarantees a website is legitimate. Without a certificate, a browser may display a warning message that the website does not have a valid certificate. Certificates can be purchased at several different providers. See a list from the California Secretary of State's website.
Back up your data
- Make a copy of your date to protect against computer failure, corrupt files, and any kind of information loss. Step-by-step directions for how to back up your files in Windows are available on my site.
See Apple's support site for back up directions on a Mac. - Storing your information in the cloud (another computer, that is server, off-site) is an option to consider. PCmag rates the best cloud storage providers. I use Google Drive, which provides 15G of free storage.
Wireless Security
One study shows that 25% of wireless connections are unsecured. Unsecured connections are open to hackers and for those that just may want to use the Internet to avoid paying for their own Internet service. If your Internet connection suddenly feels slower or you notice the lights on your router flashing rapidly when you're not using the Internet, someone else may be accessing your wireless home network.
Below is a video about a person that used a HP laptop to connect to a neighbor's unsecured network for a year and a half...until the neighbor moved. The person purchased a wireless extender hoping to reconnect to the neighbor's Internet [wireless extenders, sometimes referred to as "boosters," generally are used to extend the coverage of a router in the home, and is often used in larger homes or spaces where there is reduced coverage (dead spots)]. In the video, Wireless Access Point (WAP) is discussed. A Wireless Access Point (WAP) is a device, such as a wireless router, that allows wireless devices connect to a wired network. The person in the video does not own a wireless router and does not pay, or want to pay, for Internet service.
How to secure your wireless network
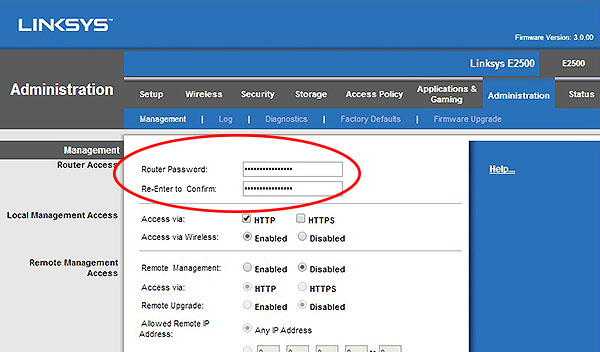
- After you set up your wireless router, change the default administrative password (typically the default password may be something like admin or password, easy for anyone to guess). See a screen capture below of the configurations for my Linksys router.
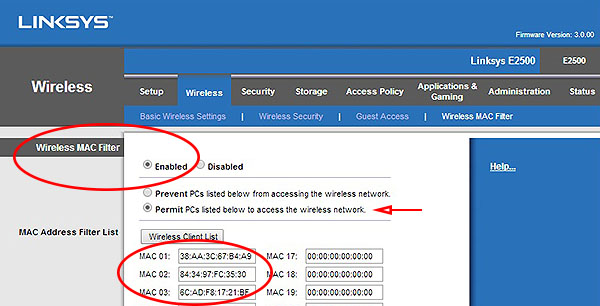
- Enable the MAC (Media Access Control) feature. Each device has a unique address. Below are the MAC addresses for three of my devices (smartphone, tablet, and Chromecast). Only these devices are allowed to connect to my wireless network.
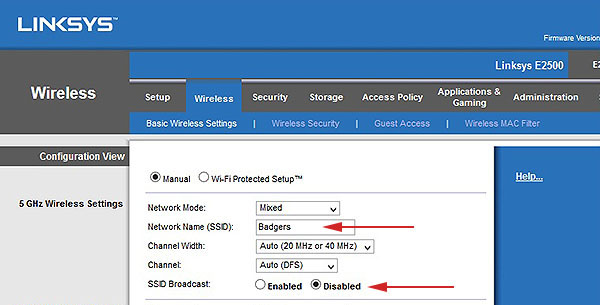
- Don't broadcast your SSID. If others (such as your neighbors) can't see it, it will be difficult for them to connect. Others must know the Network Name (and password) to be able to connect.
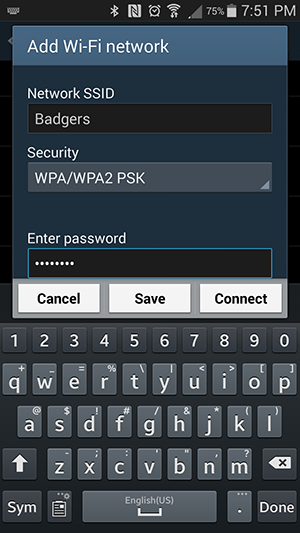
- If SSID is disabled, I won't be able to see it either when connecting a device for the first time. For example, if I need to connect my smartphone to my wireless network the first time, I need to manually enter the Network Name (along with the password) to connect.
Ethics of using computers to alter output
- Photos are often retouched, especially the magazine covers we see while waiting at the check out line at the grocery store. Ethical?
- Two photos were shot at different exposures; one to account for the brightness of the moon and the other to account for the darker foreground. Then the two photos were composited together into one photograph. Ethical?
Green Computing
- Green computing includes using power management features to save energy. The Windows operating system includes three power management features. To access these features, compare each one, and learn how to use, see my detailed pdf file.
- For Mac users, see your System Settings for each Energy Saver, Display and Security & Privacy.
- Energy Saver: dim display when using battery
- Display: automatically adjust brightness
- Security & Privacy: disable remote control infrared receiver
Disabling Wifi and Bluetooth, when not in use, will also save energy.
- Don't pollute the environment. Visit the United States Environmental Protection Agency to learn where to donate or recycle your old electronics.
There are excellent resources to help you be green. For example, if I have a Dell PC, the site provides links for me to print a shipping label and they'll pick up my old PC for free! - See Apple's recycling program.
- Facebook and Apple, among others, use mother nature to cool down their servers.
Information privacy
- In 2009, Google began customizing search results for all users. Websites collect personal data and are tailoring their sites to us. Our information is being sold to advertisers. Direct marketers say that using personal information helps target the right advertising to the right people and saves money and lowers product costs. Others feel that collecting personal information reveals more about an individual than anyone has a right to know. Want more to think about? Consider this interesting book: The Filter Bubble.
- Cookies are plain text files that are deposited onto your computer from a website you visit. Some cookies may be helpful, such as session cookies that remembers what is in your online shopping cart so that you can start shopping in one session and come back later to finish your shopping. Other cookies may store such things as your browsing habits and personal interests to target advertisements. You can use your browser to delete cookies or avoid them altogether. Below are step-by-step directions for how to delete cookies in four different browsers, which may vary slightly depending on the browser version.
- Internet Explorer: click Tools > Internet Options > General Tab. Under Browsing History, click Delete.
- Firefox: click the menu button located in the upper-right. Choose History > Clear Recent History. Click Details and select Cookies. For the time range drop-down, choose Everything if you want to delete all cookies. Finally, click the Clear Now button.
- Chrome: click the menu button located in the upper-right. Click Tools > Clear browsing data. Select Cookies... and then click Clear browsing data.
- Safari: click Preferences > Privacy. Click Details and select one or more websites that store cookies and choose Remove or Remove All.
According to a Wall Street Journal study, the top fifty Internet sites, from CNN to Yahoo to MSN, install an average of 64 cookies to track your browsing habits. Search for a word like "depression" on Dictionary.com, and the site installs 223 cookies so that other Web sites can target you with antidepressants. (Pariser).
Pariser, Eli. The Filter Bubble. Penguin Books, 2011. - Enable private browsing so that cookies and history are not saved and you don't have to worry about deleting this information later. Private browsing will help to safeguard your browsing habits.
- Internet Explorer: click Tools > Safety > InPrivate Browsing.
- Firefox: click the menu button located in the upper-right. Choose New Private Window.
- Chrome: click the menu button located in the upper-right. Choose New Incognito Window.
- Safari: click Safari > Private Browsing.
- Phishing is a trick to obtain information. It is often an official looking email that may direct you to a website that simulates a legitimate one, usually one that requires the user to log on and provide financial information. Fake email and websites for PayPal and banks have been known to exist. A telltale sign an email is phishing is when a link in the email (such as pnc.com) does not take you to the website with a matching URL (website address). You should never click links in an email that may look suspicious. See an example and learn more about what it is, why people do it, and how email is "spoofed."
To help guard against phishing scams, enable your browser's phishing filter. Below are step-by-step directions for how to enable phishing filters in four different browsers, which may vary slightly depending on the browser version.
- Internet Explorer: click Tools > Safety > Turn On Smart Screen Filter
- Firefox: phishing filter is built in the application and is turned on by default. The options are found on the security panel:
click the menu button located in the upper-right. choose Options > Security. You should see a check mark next to "Block reported attack sites" and "Block reported web forgeries." - Chrome: click the menu button located in the upper-right. Choose Settings. Click the Show advanced settings link and then find the "Privacy" section. Be sure the box is checked for "Enable phishing and malware protection."
- Safari: Settings > Safari. Be sure anti-phishing feature is turned on.
Want to be sure your browser phishing filters are turned on and doing their job? Try this test. This is a phishing site and your browser should warn you.
- Fake emails have been sent to represent eBay. eBay allows you to report fake emails on their site.
- Spyware and Adware. Spyware monitors your activities. Adware displays annoying advertisements. Learn more, including links for software to detect and clean infected computers.
